Extend Zero Trust to Your Autonomous Infrastructure
Defakto helps enterprises enable Zero Trust for workloads, APIs, machines, and AI agents. No long lived credentials. No shared secrets. Just real-time, verifiable identity.
Challenges
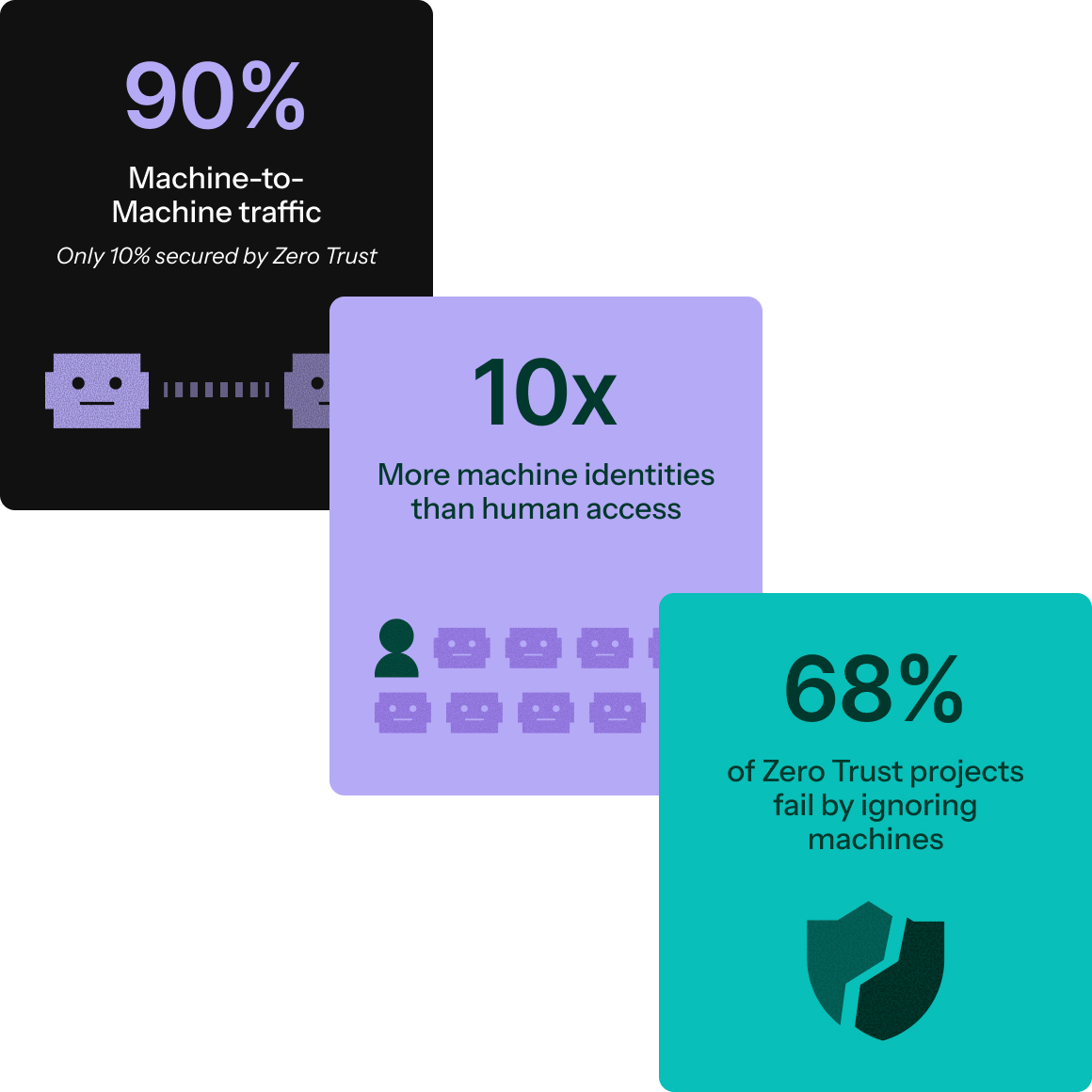
Non-human identities: Zero Trust’s blind spot
Zero Trust has secured people with MFA and access policies. But most activity in the enterprise isn’t human. It’s service accounts calling APIs, workloads talking to workloads, and AI agents making decisions autonomously. These non-human identities are still trusted by default, running on long-lived secrets and broad permissions. That blind spot sits outside the Zero Trust model, leaving the core of the infrastructure exposed
Defakto closes the blind spot
Defakto replaces static secrets with short-lived, verifiable identities for every automated interaction. Access is scoped by policy, continuously verified, and fully auditable. Instead of implicit trust, every interaction is authenticated, authorized, and accountable bringing Zero Trust to the systems your infrastructure depends on.
Defakto = Zero Trust for every automated interaction
Defakto brings identity-based access controls to non-human actors the same way human IAM does for people. But instead of usernames and passwords, Defakto issues real-time, short-lived identity with built-in verification.
- No long-lived credentials
- No over-permissioned service accounts
- No reliance on static network rules – access is based on identity, not IP addresses or location.
Every request is backed by verifiable identity. Every action is scoped to what’s needed and nothing more.
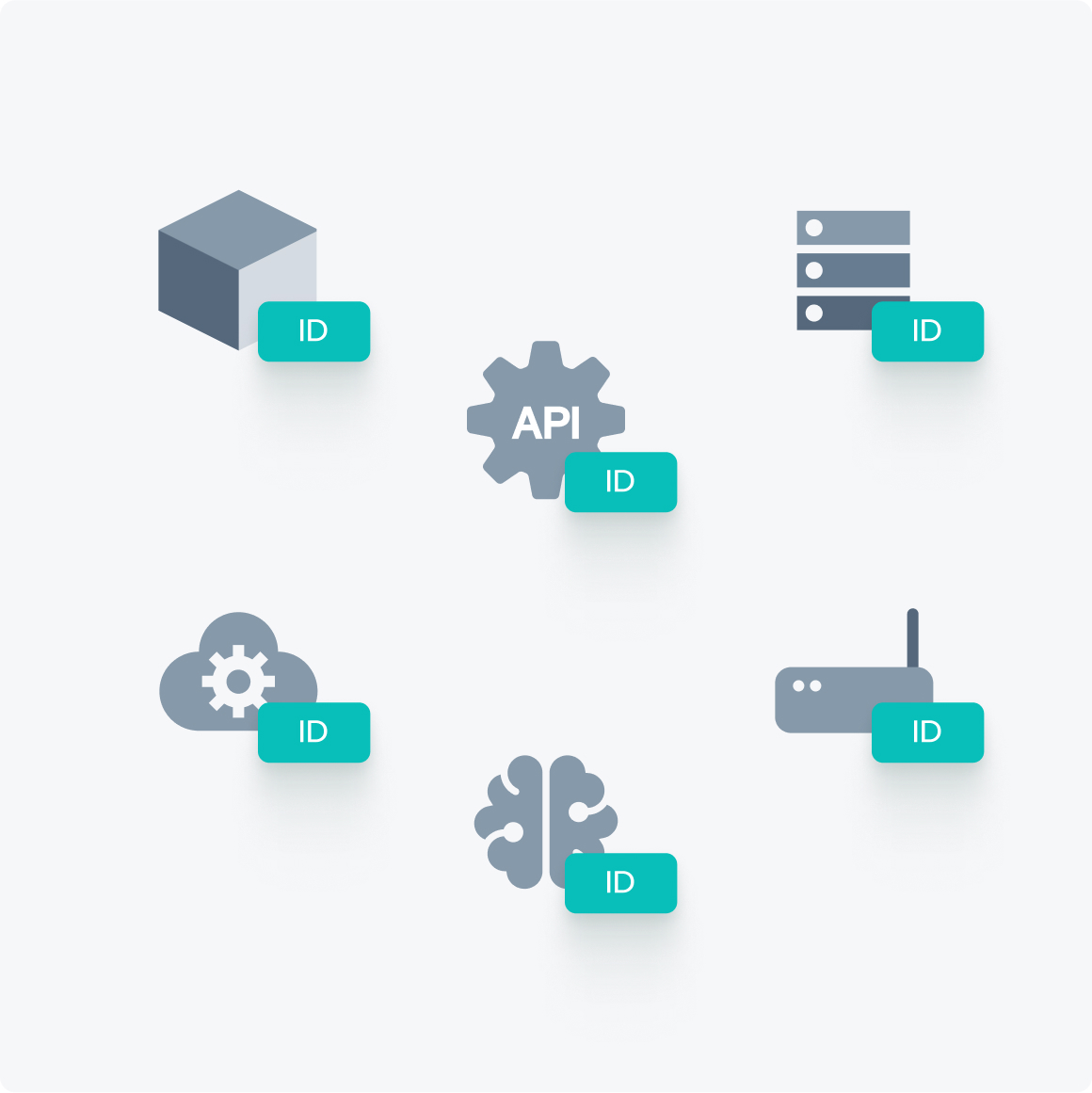
Defakto secures the infrastructure that humans don’t log into
If it moves data or makes decisions, it needs a Defakto identity.
Zero Trust isn’t complete unless it covers every actor in your environment. Defakto is built for:
Outcomes that accelerate Zero Trust
Reduce attack surface. Accelerate adoption. Shrink technical debt.
Defakto helps security teams make measurable Zero Trust progress for Non-Human Identity
Reduce attack surface
Eliminate long-lived secrets and blind spots in east-west traffic
Enforce least privilege
Issue scoped, time-bound identities
Simplify access reviews
No more orphaned service accounts or legacy PAM sprawl
Accelerate rollout
Integrates with your existing stack and existing controls
Enable compliance
Map NHI governance to NIST and Zero Trust mandates