From Secret Sprawl to Zero Secrets Architecture
Defakto eradicates static secrets by issuing short-lived identities at runtime. No vaults. No rotations. No humans in the loop.
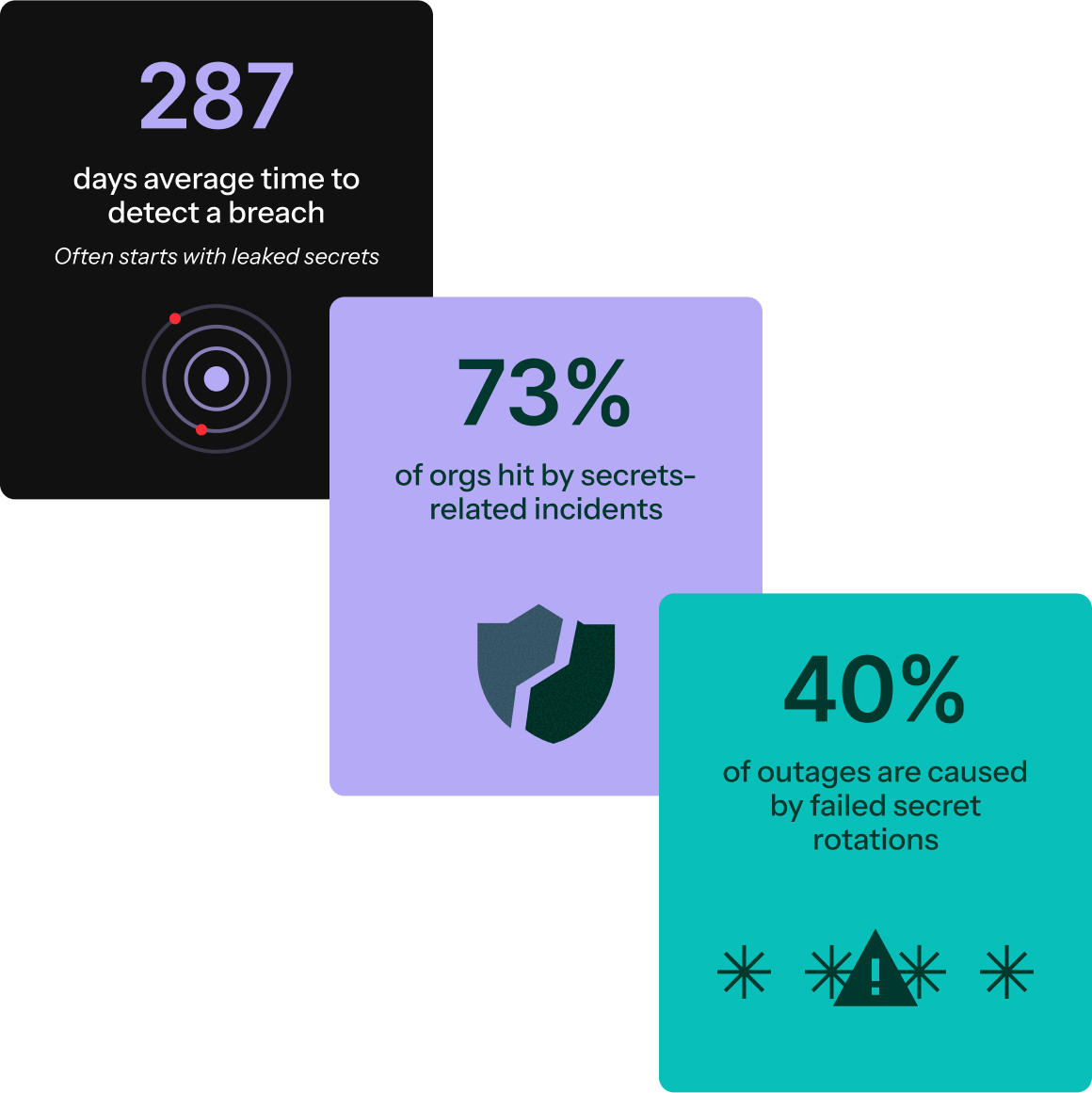
Challenges
Secrets are breaking security
Secrets don’t just leak. They break builds, cause outages, and hide risk in the systems that automate and scale your business. From OAuth client secrets and database passwords to Cloud and LLM API keys, these static credentials are everywhere. Designed for a different era, they don’t fit today’s non-stop code pipelines, autonomous AI agents, or dynamic service-to-service networks. As companies scale, there is more automation, more cost, less oversight, and an attack surface growing faster than security can keep up.
Defakto eliminates the hidden risk in your stack
Traditional secrets management leaves secrets sprawl in place. Defakto removes the need for secrets entirely, issuing short-lived, verifiable identities for every workload, pipeline, and AI agent. No hardcoded keys, no over-permissioned accounts, no hidden credentials, no escalating costs. A modern and resilient approach that scales as fast as your infrastructure.
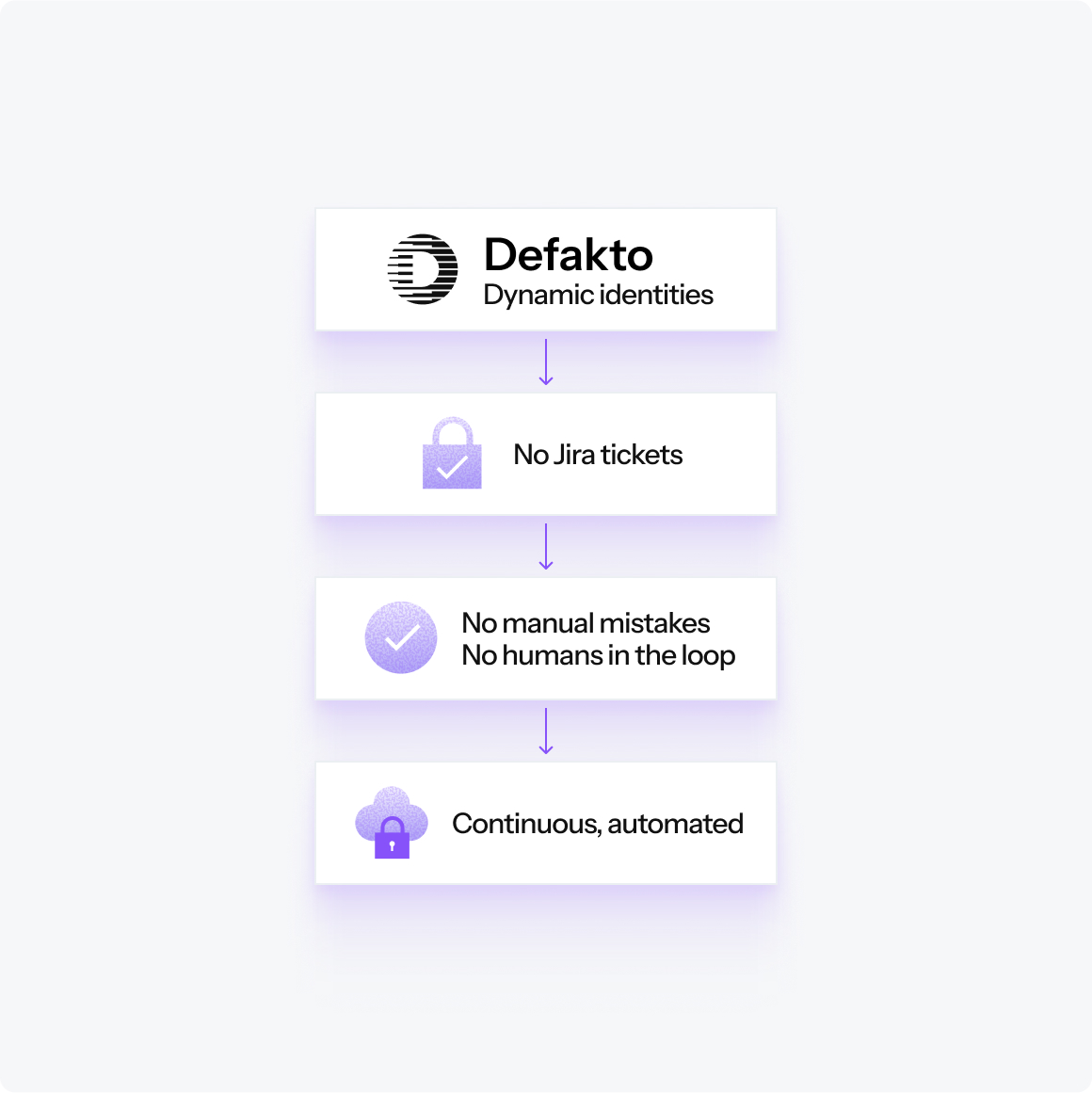
From secrets to identity: a new model for securing automation
Defakto secures your infrastructure by removing humans from the loop and replacing every static secret with short-lived, purpose-bound identity.
When a CI/CD job runs, a container starts, or an AI agent calls an internal service:
- Defakto evaluates context in real time
- Then issues a verifiable identity, scoped to its role and need
- No standing access. No long-lived secrets. No ticket queues or manual approvals
Access is automatic, auditable, and enforced through identity—not secrets.
Defakto Capabilities
Replace secrets with real-time identity
Defakto Business Impact
What you get when secrets go away
Fewer outages, better compliance, stronger Zero Trust — here’s the business value of replacing secrets with identity.
Reduce blast radius
Without static credentials, there’s nothing to steal, leak, or use to move laterally. Access is scoped, verified, and temporary.
End identity debt, cut costs
Secrets pile up risk and expense. Defakto replaces them with self-governing identity that eliminates both.
Increase system resilience
Misconfigured secrets and expired tokens no longer cause outages. Identity is issued dynamically. No manual rotation, no error-prone dependencies.
Unify security and operations
Defakto simplifies access control across environments. Security teams gain visibility. DevOps gains speed. No more fire drills.
Build zero trust
Ephemeral, policy-enforced identity ensures workloads only access what they should and when they should.
Pass audits without the scramble
Every access event is logged, attributed, and verifiable. No shadow credentials. No undocumented access.