Secure Agentic AI and LLMs. Accelerate Adoption.
Replace hardcoded API keys with dynamic identities. Every agent is authenticated, authorized, and audited in real-time. Defakto gives every AI agent a verified identity, scoped access, and full activity logs ensuring trust, governance, and speed at scale.
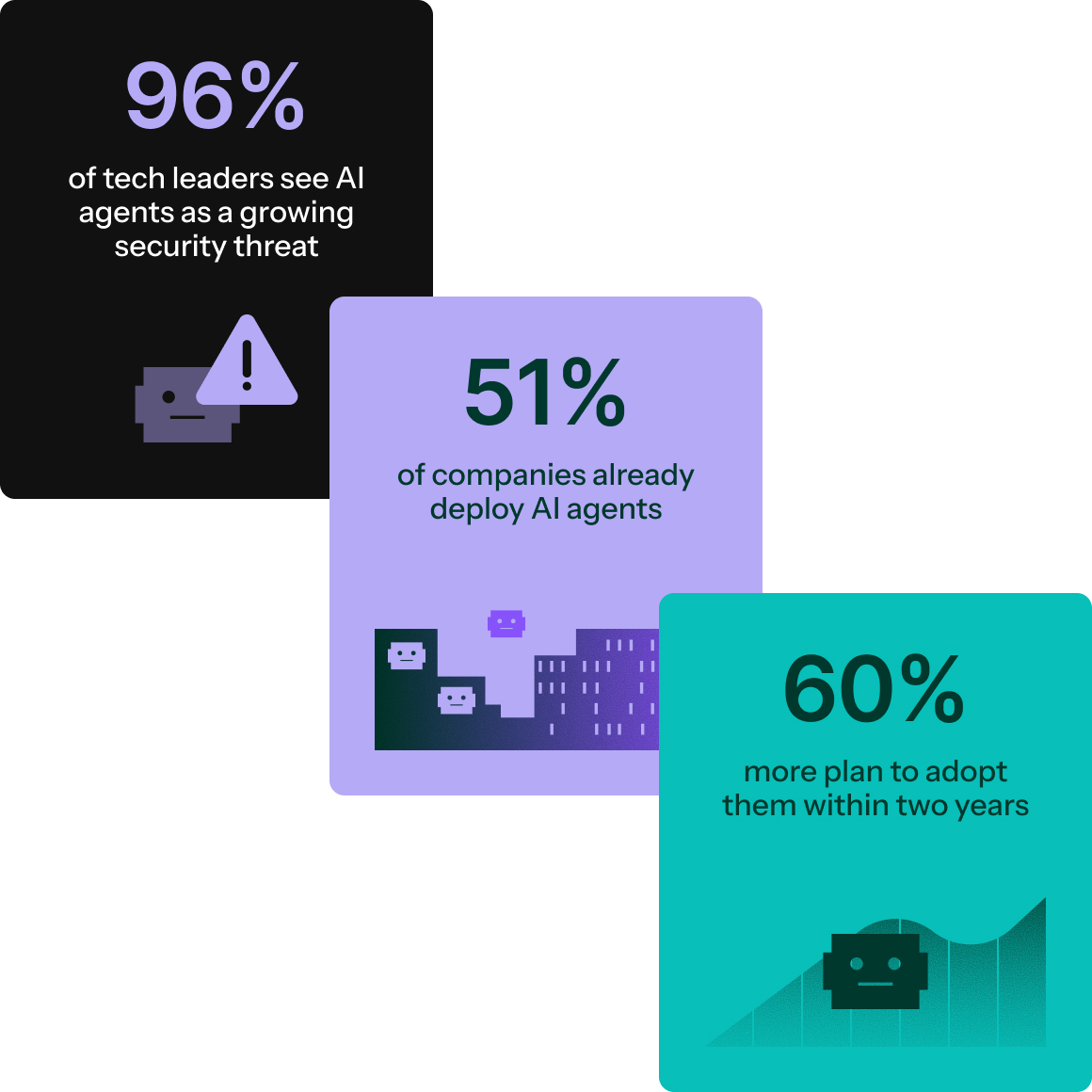
Challenges
AI agents are the newest, and riskiest, kind of identity
AI agents aren’t just answering questions; they’re booking meetings, moving money, and accessing customer data. But they authenticate like it’s 2005: hardcoded API keys, scattered across repos and environment files. One leaked OpenAI key doesn’t just cost you credits; it exposes every conversation, every prompt, every piece of data your agents touch.
Every AI application begins with an LLM API key. As agents move from proof of concept to production, keys and secrets multiply across environments — with no lifecycle controls for rotation, revocation, or governance. A single leaked or misused key can trigger outages or expose sensitive data, and most providers offer no way to manage this at scale.
Teams are under pressure to experiment and drive more productivity and automation. Beneath the excitement is a fragile foundation of hardcoded keys, scattered secrets, and ad-hoc access, creating blind spots and risk as organizations push to innovate. Any useful AI application connects to confidential data and acts across enterprise and third-party services — power that must be secured to eliminate risk.
Stop managing keys.
Start managing AI.
The average Agentic AI application uses an LLM API key, and multiple secrets to connect to enterprise data and applications. These credentials are unmanaged and rarely rotated, leaving teams blind to usage.
With Defakto, every AI agent and workload receives a verifiable, short-lived identity that enforces policy, authenticates without secrets, and logs every action. These identities enforce policy, authenticate without secrets, and log every action to a cryptographically auditable trail. By automating the full identity lifecycle, Defakto eliminates API keys and access blind spots so enterprises can adopt AI with speed, governance, and confidence from proof of concept through production.
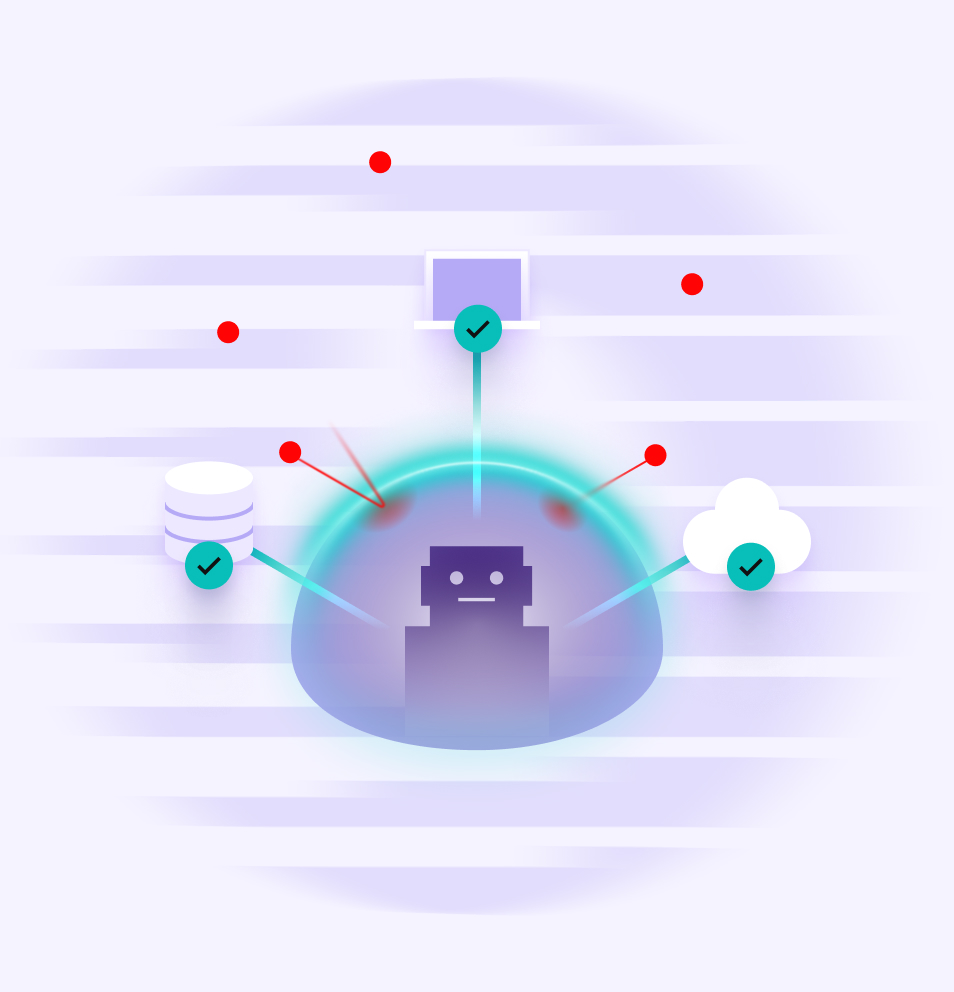
Control AI access with Defakto
Give AI agents verified identities to enforce policy, audit activity, and prevent overreach. Each identity is issued at runtime, scoped by policy, and fully logged no matter where the agent runs or who built it.
So instead of hardcoded API keys or wide-open backend access, your AI agents can:
- Prove who they are
- Only access what they’re supposed to
- Leave behind a full audit trail
Whether you’re integrating AI across departments or running a self-hosted model in production, Defakto ensures AI works inside your rules, not around them.
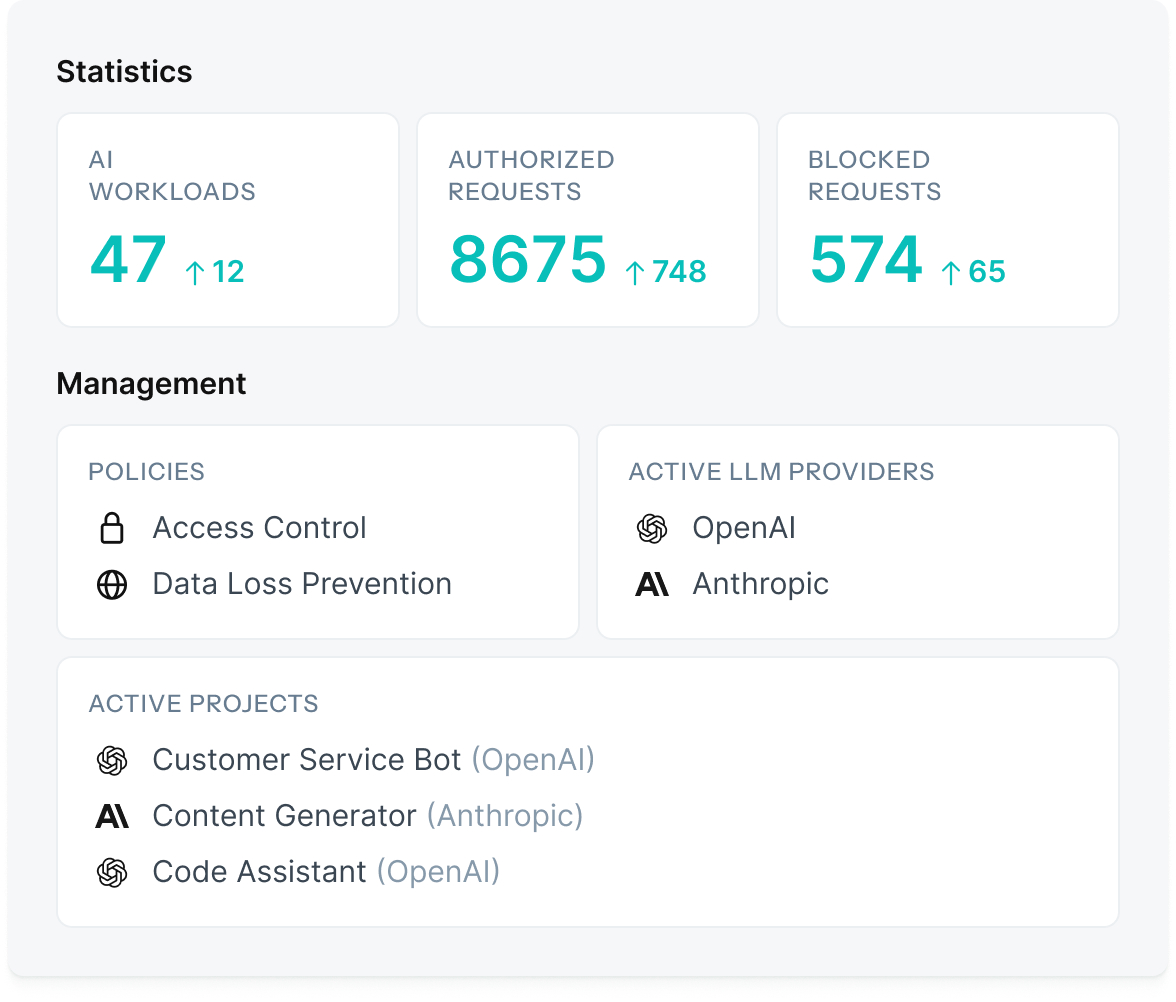
Delivering AI controls at scale
Defakto’s Non-Human IAM Platform Capabilities
AI systems scale unpredictably, making manual credential management unworkable. Defakto automates the identity lifecycle, enabling teams to innovate without added risk or overhead.
Defakto Business Impact
Unlock the full potential of AI without the risk
Scale adoption, protect sensitive data, and prove governance with identity-first security for every agent.
Accelerate adoption without compromise
Identity lifecycle automation empower teams to move fast with security teams fully onboard.
Prevent data leaks and IP exposure
Keep sensitive systems off-limits even to smart agents.
Gain visibility and control
Know what your AI is doing, where, and why.
Prove governance, satisfy audits
Show you’re in control of even your most autonomous systems.
Secure your AI destiny
Prevent the next breach instead of explaining the last one.