Non-Human IGA for Modern Infrastructure
AI agents, workloads, APIs, and service accounts now outnumber human users. Defakto extends identity governance to every non-human actor delivering control, visibility, and compliance without legacy overhead.
Challenges
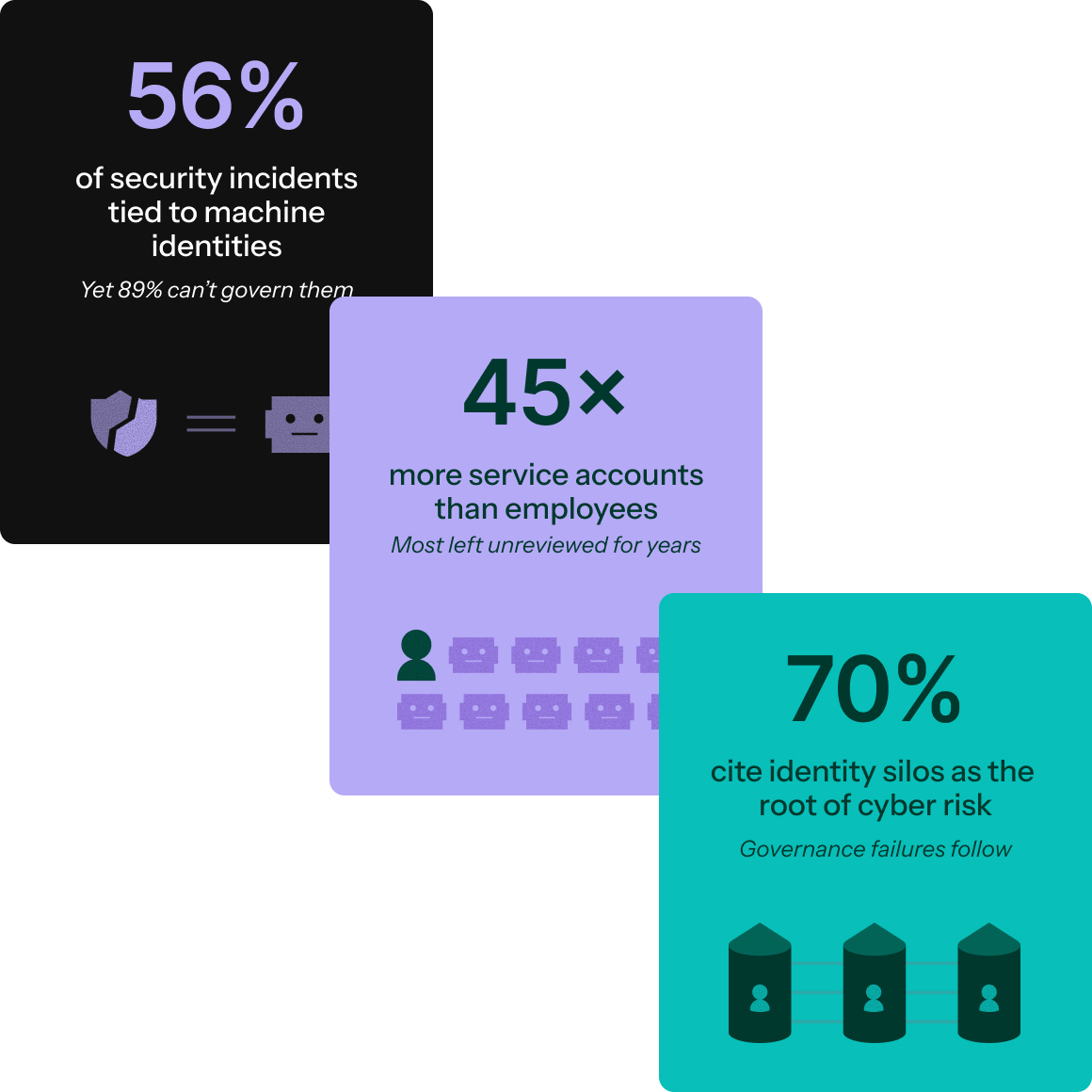
The governance gap with NHI
Every API call, every automated deployment, every AI agent runs on a machine identity. But while you govern human users with policies, approvals, and reviews, your service accounts get permanent access with no oversight. Legacy IGA wasn’t built for machines, and the gap is getting dangerous.
Defakto: Govern machines like you govern people
Defakto applies the same governance rigor to machines that you already use for humans: just-in-time access, policy enforcement, continuous review, and complete audit trails.

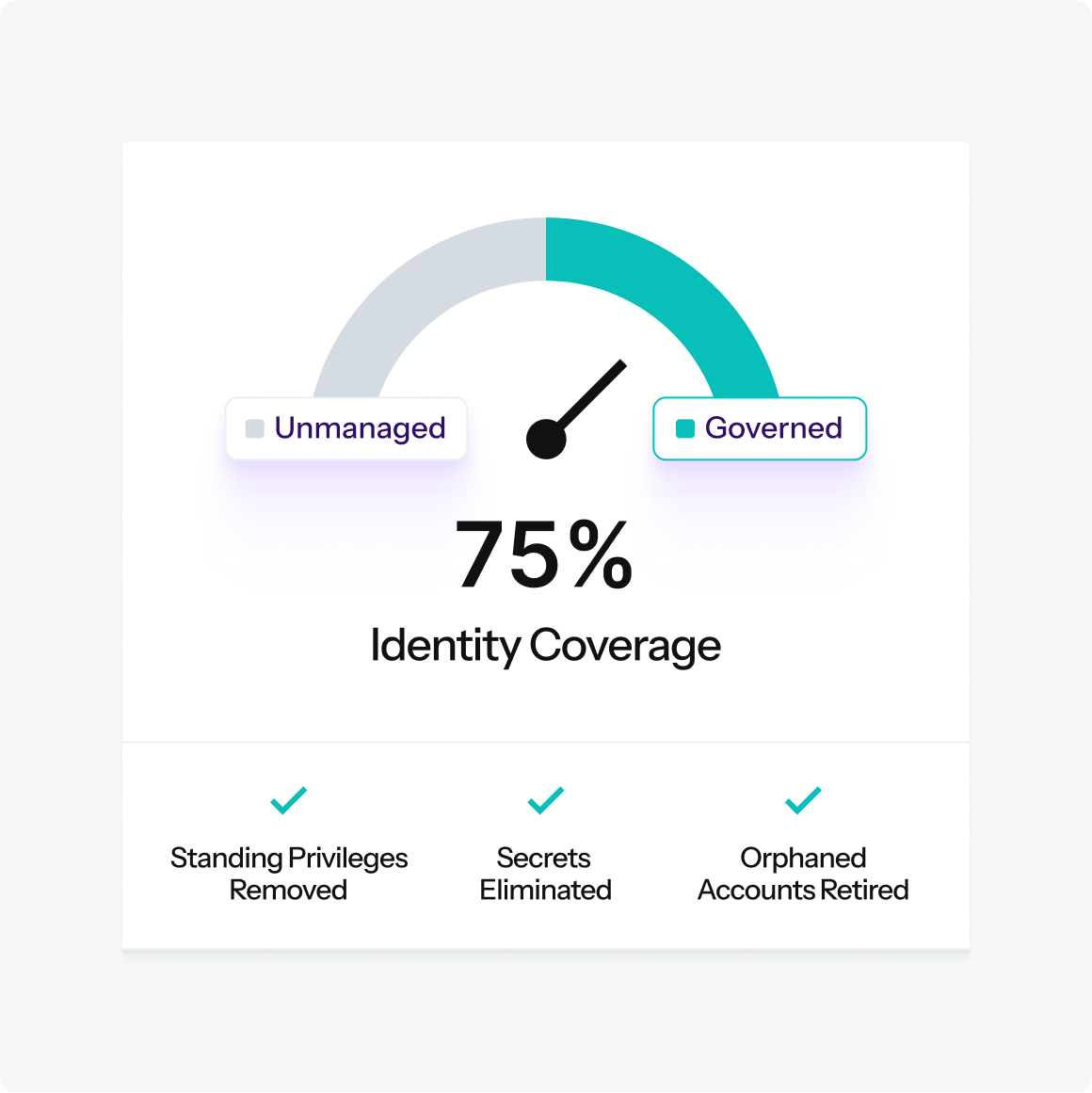
Complete your IGA strategy
Your IGA system governs 10,000 employees but ignores 450,000 service accounts. Defakto extends governance to every machine identity without the manual overhead that makes traditional IGA painful. Most enterprises carry identity baggage that traditional IGA never fixed. Defakto clears it out by replacing error-prone, static approaches with dynamic governance built for NHI.
With Defakto, you can:
- Remove standing privileges
No more accounts with perpetual access just waiting to be abused. - Eradicate secrets
Eliminate hardcoded keys, config files, and vault sprawl that attackers target. - Retire orphaned & over-privileged service accounts
Replace years-old accounts with identities that only exist when needed. - Automate certificate & token management
Identities are minted and retired on demand. No CSR requests, no manual ticket queues, no rotation headaches. - Unify auditability
Stop piecing together logs; every machine action ties back to a governed identity.
Capabilities that complete IGA for NHI
Defakto extends governance beyond people to every machine, workload, and AI agent. By embedding lifecycle control and policy enforcement into your infrastructure, Defakto makes IGA complete and keeps it aligned with Zero Trust principles.
What Defakto adds:
With Defakto, you gain the missing governance layer for non-human identities, while reinforcing least-privilege access and Zero Trust resilience across your environment.
Business outcomes that matter
Turn identity governance into business advantage
Defakto helps security and infrastructure leaders achieve outcomes that extend beyond compliance. By governing non-human identities at scale, you reduce risk, cut costs, and accelerate strategic initiatives.
Reduce attack surface
Eliminate standing access, orphaned accounts, and unmanaged secrets across your environment.
Accelerate Zero Trust adoption
Fill a critical gap in your Zero Trust strategy by extending governance to all machine and AI identities.
Improve audit and compliance readiness
Gain clear, auditable logs of all non-human identity activity: who accessed what, when, and why.
Streamline security operations
Automate identity lifecycle and access decisions to reduce manual effort and avoid costly misconfigurations.
Enable safe innovation
Adopt new cloud, DevOps, and AI technologies without expanding your risk footprint.