Go Accountless. Eliminate Service Account Risk Forever
Eliminate long-lived service accounts with dynamic identity. No static credentials. No standing access.
Challenges
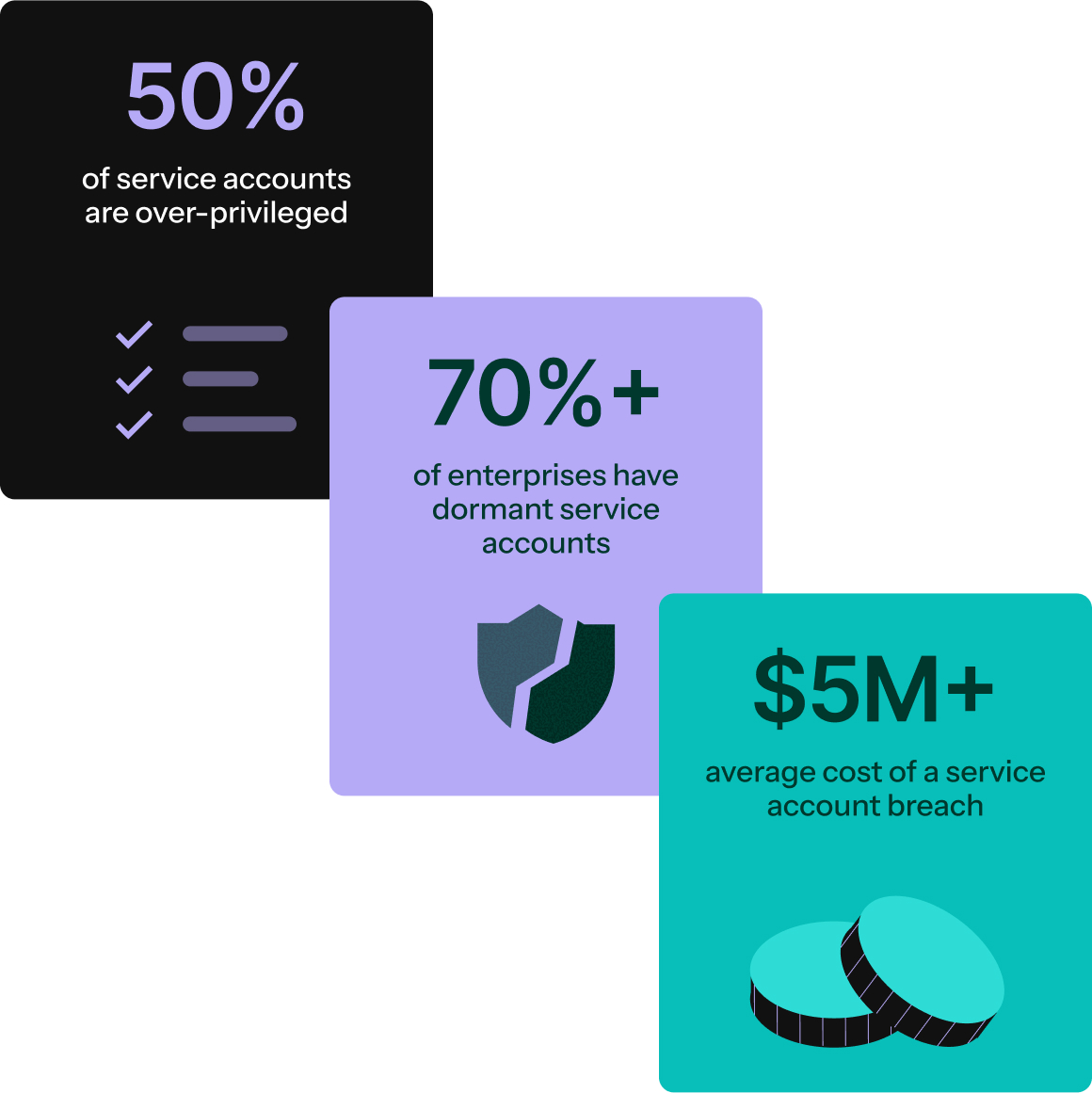
When service accounts become liabilities
Service accounts were built for a simpler era, but they’ve become a major source of risk and technical debt. They’re static, rarely rotated, over-permissioned, and hard to track. Outages and security incidents regularly stem from forgotten or mismanaged accounts, yet they continue to pile up as businesses scale with more automation and services.
Defakto reduces risk and complexity
Defakto replaces sprawling service accounts with an identity model built for automation. It issues short-lived, verifiable identities that cut down standing accounts and shrink the attack surface. For accounts that remain, Defakto enforces least privilege, continuous attestation, and full audit trails, giving IAM teams fewer credentials to track, less access to manage, and a safer, simpler way to secure and govern modern infrastructure.
From static accounts to dynamic identity
Instead of relying on static service accounts, Defakto issues just-in-time, verifiable identities that automatically expire once they are not needed. Access isn’t pre-assigned or left behind; it’s created when needed and removed when the task ends. The result: fewer standing accounts to manage, tighter access controls, and less risk across the stack.
- No shared accounts across teams or environments
- No broad default access based on group membership
- No lingering credentials waiting to be exploited
The natural outcome: fewer accounts, less overhead, and stronger security without changing how teams build and ship.
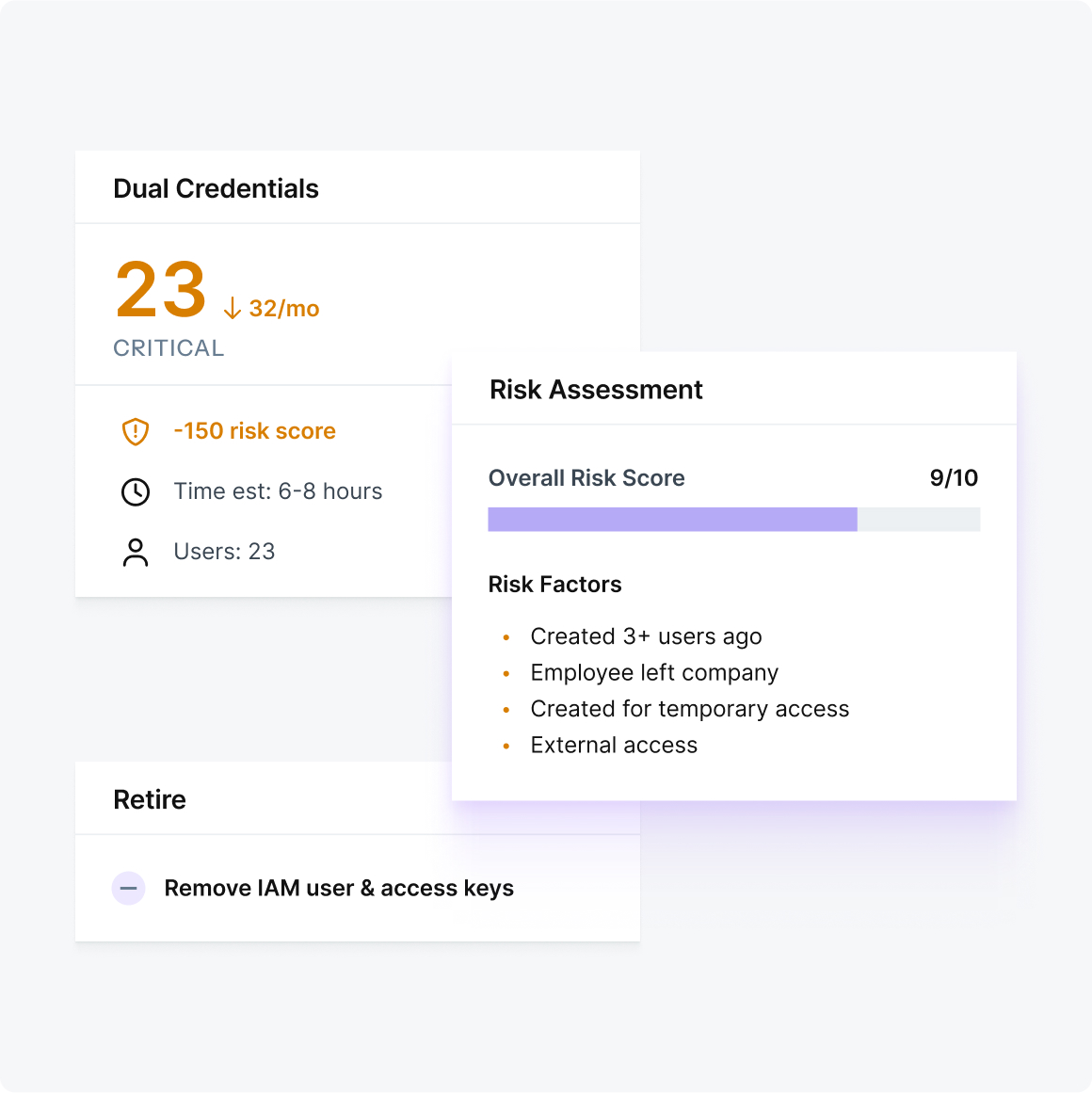
Defakto’s Non-Human IAM Platform capabilities
Defakto Business Impact
What you get when going accountless
Defakto makes your environment more secure, more resilient, and easier to manage — with fewer moving parts.
No more standing privileges
Temporary, scoped identity replaces risky, always-on access.
Fewer outages from rotations
Credentials that don’t exist don’t need to rotate.
Reduced IAM and IT overhead
No more account sprawl. Identity is issued when needed, by policy.
Kill over-permissioned access
No “just in case” entitlements. Every access request is narrow and logged.
Zero trust, enforced by design
Identities are ephemeral and policy-bound with no shared backdoors or shadow access.