Stop On-Prem Breaches Without Disrupting Business-Critical Systems
Transform legacy systems with dynamic identities. No Downtime, No Rewrites, No Excuses.
Challenges
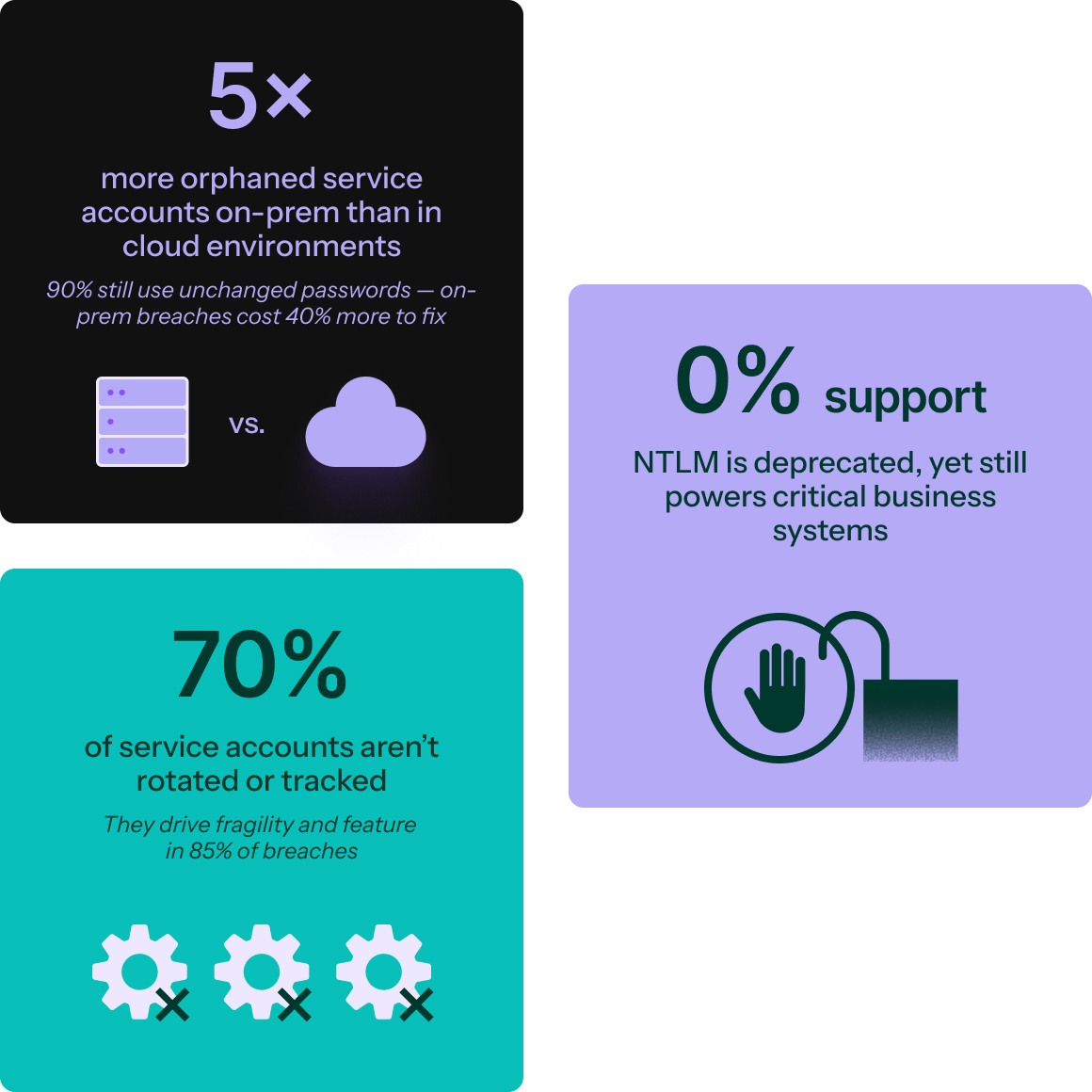
Decades of static credentials piling up
Even as enterprises modernize, critical systems remain on-prem including data centers and private clouds to legacy apps, mainframes, and edge servers. But these environments often depend on overprivileged service accounts, long-lived secrets, and error-prone certificate management. Sprawl grows as these credentials connect into cloud and SaaS, creating hidden attack paths, operational toil, and governance gaps.
Fixing the hidden risks in legacy systems
Defakto brings modern identity to every on-prem environment, eliminating secrets and unifying governance across legacy and cloud-native systems.
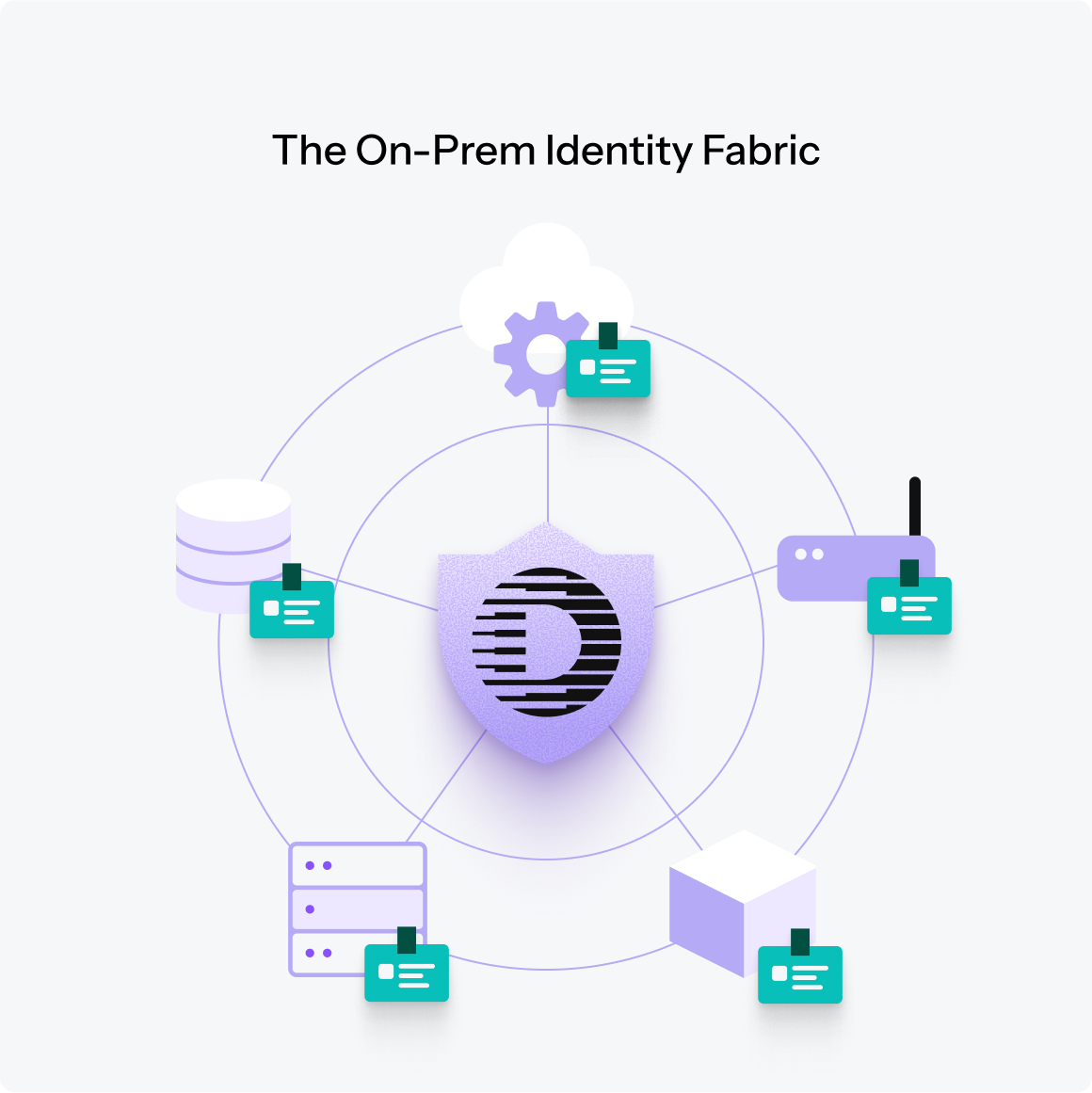
Defakto’s universal identity model for on-premises
Defakto replaces static credentials and service accounts with short-lived, verifiable identities for all non-human actors, from servers and VMs to internal services and edge devices.
- Eliminate Active Directory sprawl and reduce AD service accounts by 90%
- Replace error-prone certificate management and end certificate expiration outages
- Enforce least privilege for apps, services, and workloads on-prem
- Govern access consistently across private infrastructure and cloud
- Gain visibility into every request, certificate, and connection
Capabilities
Delivering controls for on-premises
Business outcomes
Secure legacy without disruptions
Protect critical on-prem systems without rewrites or downtime. Here’s what Defakto makes possible for your on-prem environments:
Protect critical systems
Secure the workloads that keep the business running, even if they can’t move to the cloud.
Reduce risk
Legacy systems are no longer isolated; remove unmanaged accounts, static secrets, and error-prone certificates.
Bridge to the future
Strengthen on-prem security today while preparing for hybrid and cloud tomorrow.
Simplify compliance
Unified visibility and controls across legacy and regulated systems.
Lower operational burden
Eliminate manual rotations, credential sprawl, and fragmented IAM practices.