Stop Multi-Cloud Identity Chaos. Unify Access Everywhere.
Unify non-human identity, simplify access, enforce least privilege. Everywhere.
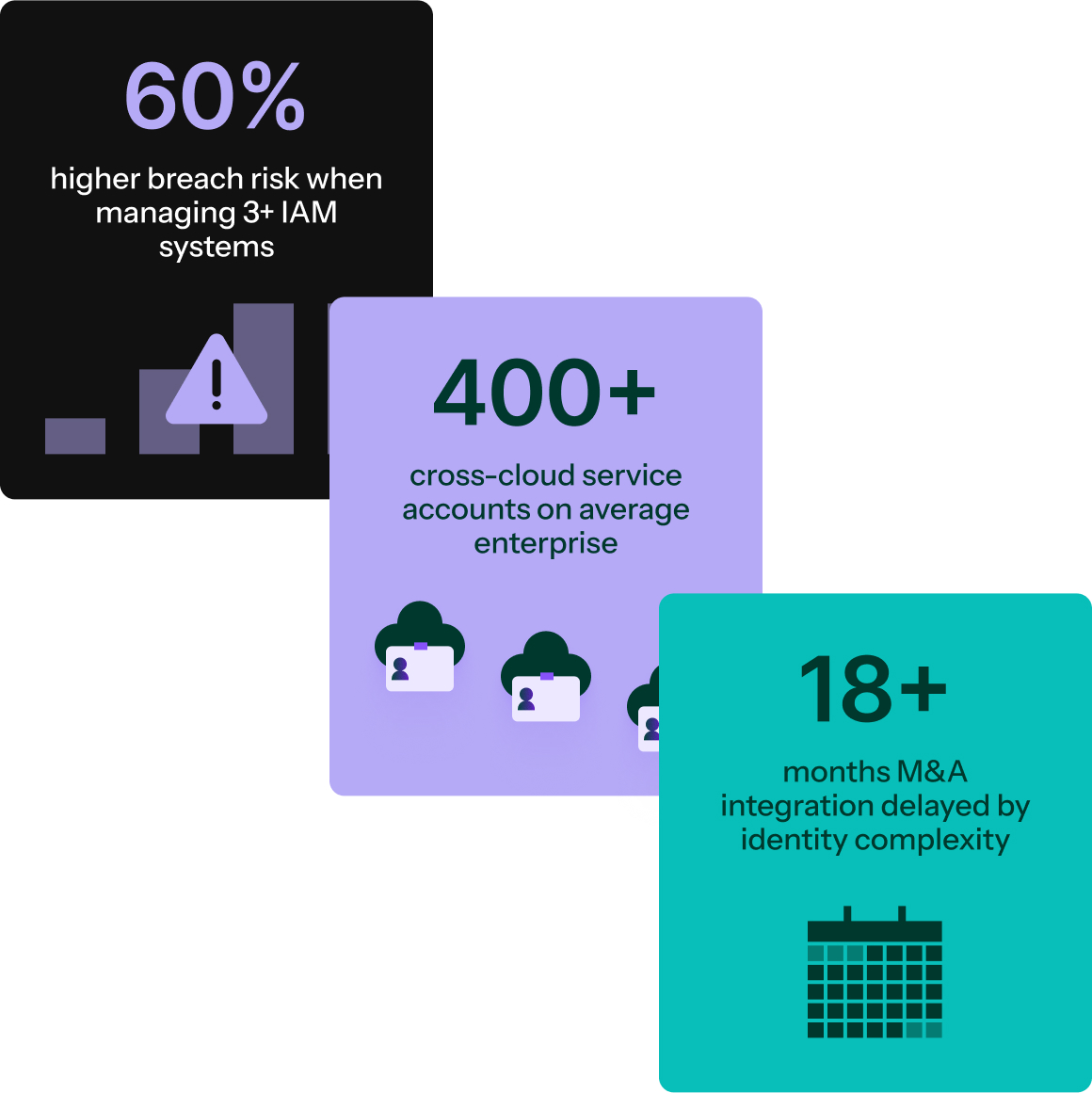
Challenges
The growing risk in cloud and serverless
Some enterprises design for multi-cloud to avoid lock-in, meet regulatory demands, or optimize performance and cost. Others inherit it through M&A or team-driven choices such as a data team in GCP, developers in AWS, research in Azure, vendors on their own platforms. Either way, organizations end up juggling different IAM models, patching gaps with static secrets and overprivileged roles. The result: fragmented governance, greater complexity, and an expanded blast radius without a unified identity.
Defakto eliminates credentials, not velocity
Instead of embedding and managing secrets, Defakto issues short-lived, verifiable identities directly into pipelines. Credentials are created just-in-time, scoped to the job, and expire automatically when tasks end. Developers don’t need to create, rotate, or clean up credentials. Pipelines stay fast, secure, and auditable without the overhead of secret
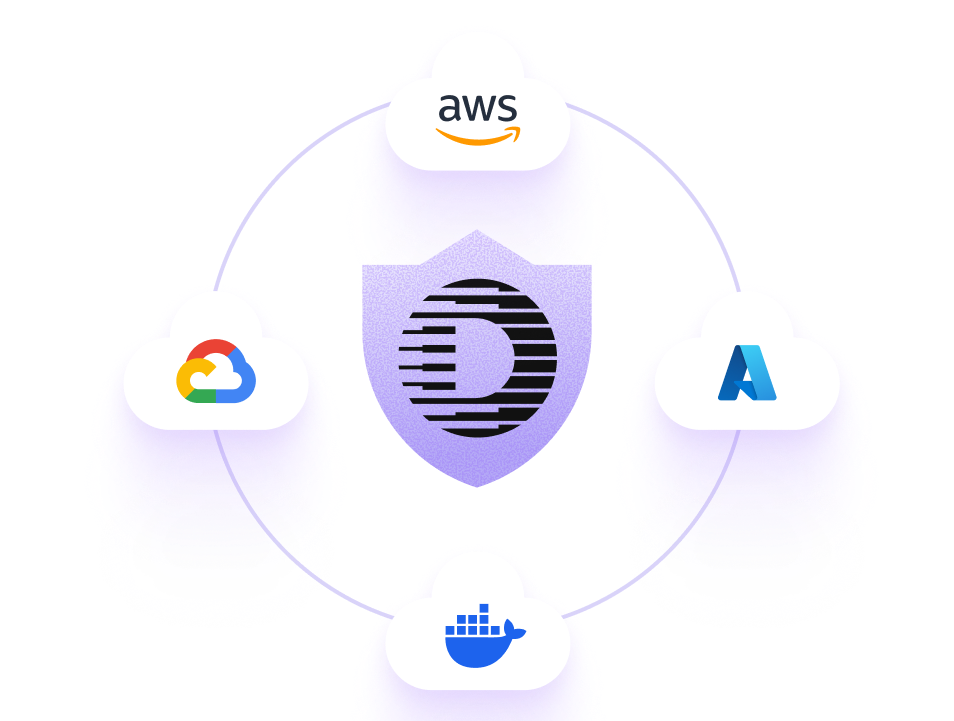
Defakto’s universal identity model for multi-cloud
Defakto unifies non-human identity across clouds by replacing static credentials with short-lived, verifiable ones. Every workload, container, and function receives a secure identity at runtime, governed by consistent policy everywhere.
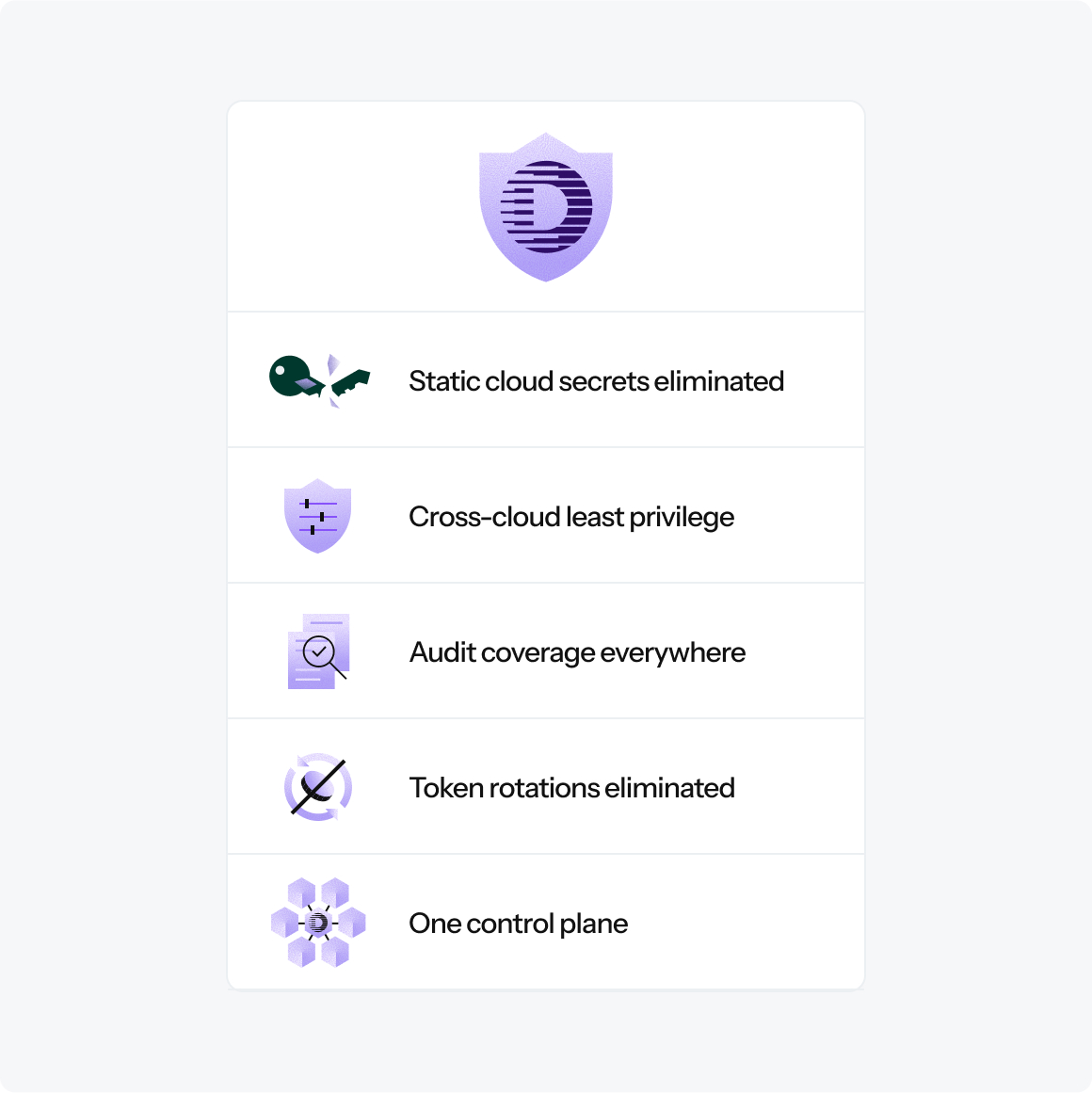
- Eliminate static secrets → Eliminate 100% of static cloud keys
- Enforce least privilege consistently across AWS, Azure, and GCP
- Automate identity issuance and lifecycle management
- Unified visibility→ Single dashboard for all cloud access
Delivering controls at scale
Defakto Business Impact
The payoff of universal identity at scale
Less risk, less overhead, more control all without rewriting your cloud strategy.
Reduce exposure risk and blast radius
No static secrets, no unchecked roles, no sprawling attack surface.
Simplify compliance
Unified governance and auditability across providers.
Unlock value from M&A
Integrate acquired environments without IAM chaos.
Enable innovation and choice
Run workloads in the best cloud for the job, without security trade-offs.
Gain visibility and control
See which workloads have access to what, ensure permissions align with policy, and eliminate unused or excessive entitlements.
Lower operational burden
Automate identity issuance and policy enforcement, reducing human error and overhead.
Simplify compliance and audit
Every action is auditable, making compliance and regulatory reporting available in real time.