Secure Kubernetes Without Secrets
Eliminate static credentials with just in time workload identity.
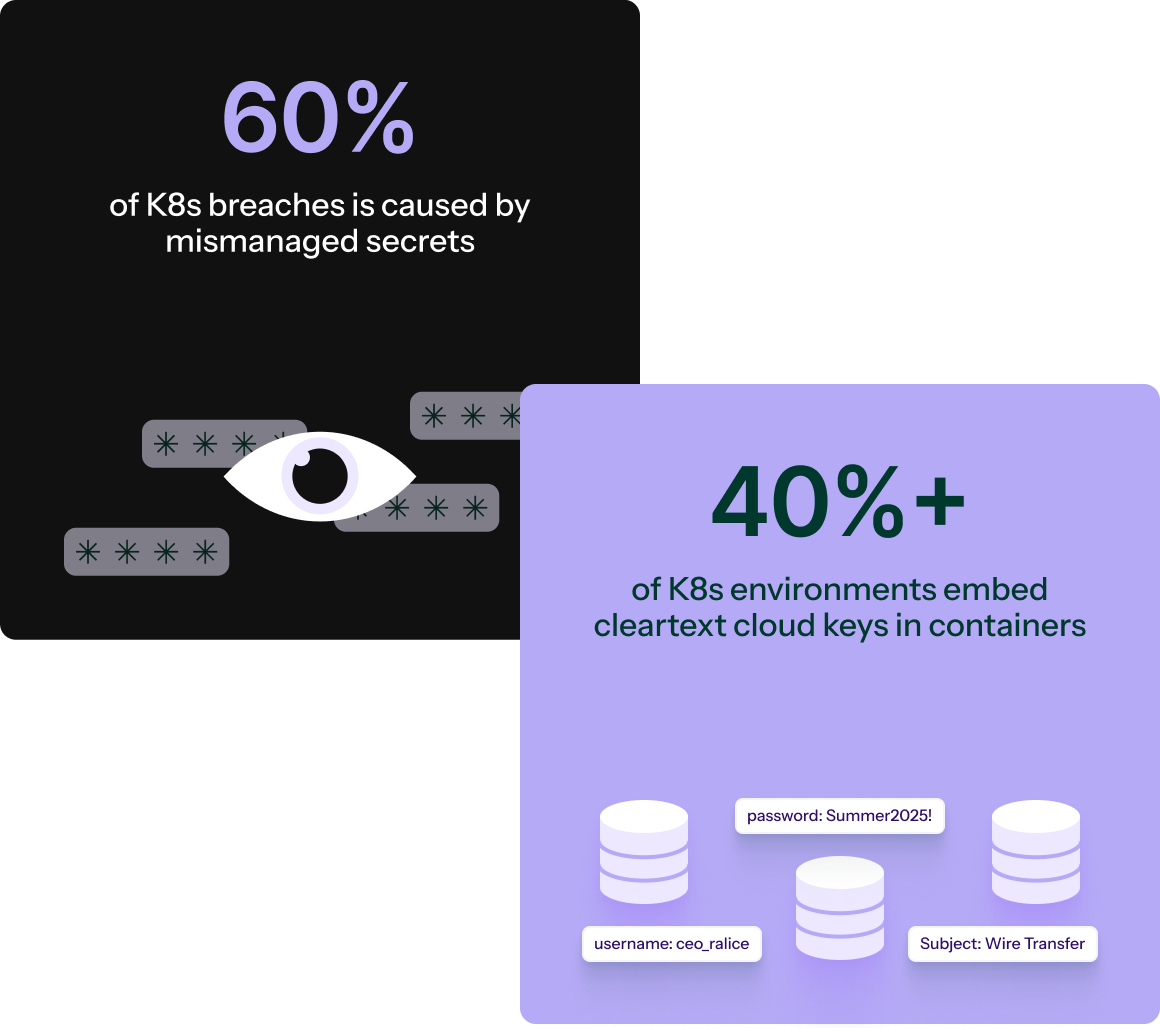
Challenges
Kubernetes delivers speed, but its default identity model creates risk.
- Secrets sprawl across YAML, Config files, and vaults.
- Workloads depend on service account (bearer) tokens that, once stolen, can be replayed.
- Cluster components rely on brittle certificates and manual PKI processes.
- Admins use Kubernetes credentials that linger on laptops and repos.
Even in managed clusters, the problem persists. Credentials are scattered, long-lived, and difficult to rotate. One leaked secret can give attackers persistence, lateral movement, and control which can turn Kubernetes’ velocity into a security liability.
Defakto eliminates secrets, not scale
The answer isn’t better vaults or faster rotation. What’s missing is an identity-first foundation. Security needs proof and visibility, while platform teams need an approach that won’t slow down delivery.
Defakto closes this gap by extending modern identity into Kubernetes. Instead of patching together secret managers and error-prone manual processes, Defakto provides a single trust model across applications, pods, services, clusters, and even service meshes. The result: Kubernetes enables rapid innovation at enterprise scale, with the resilience and guardrails required for security and compliance — while extending trust seamlessly across cloud-native, bare-metal, and traditional on-prem systems.

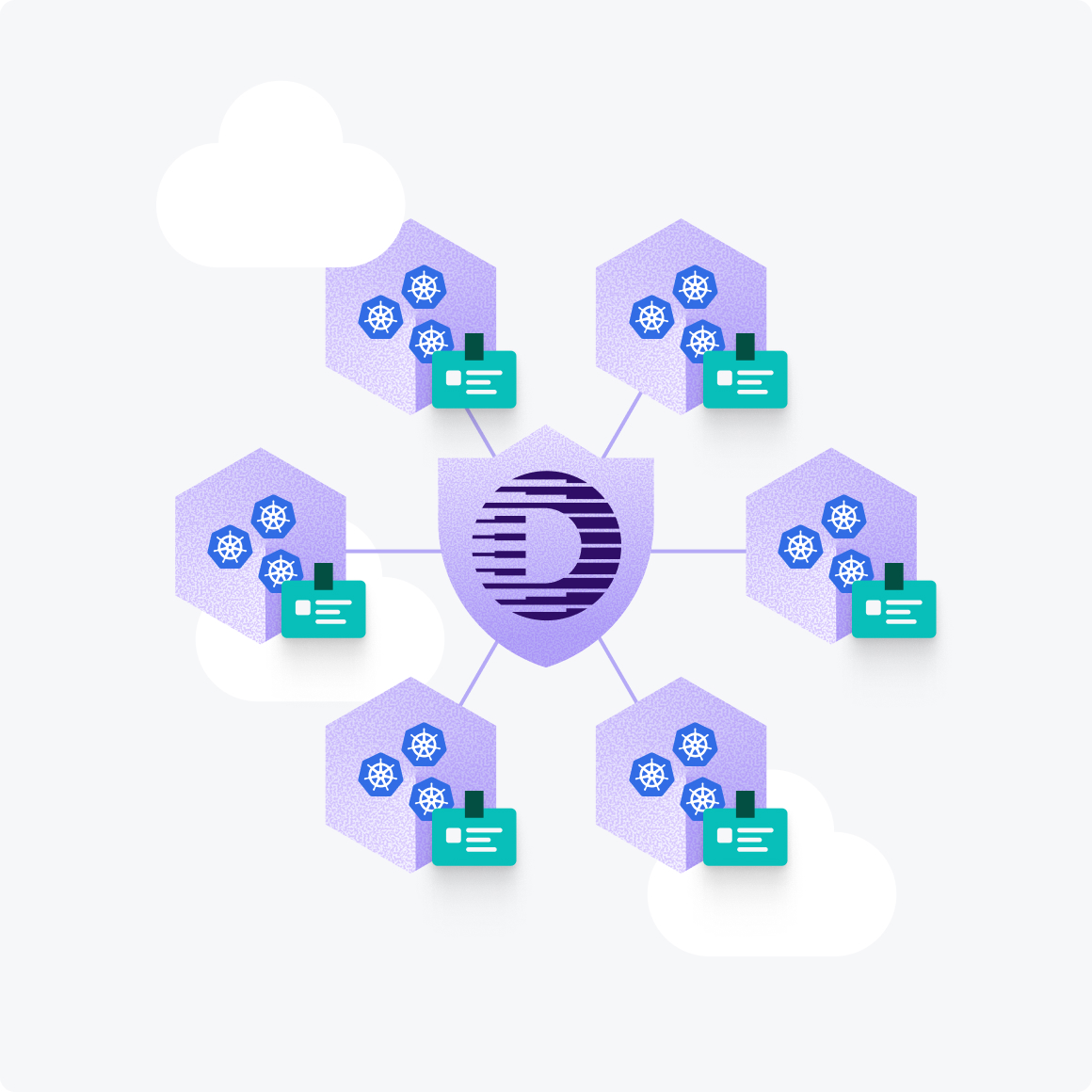
The Defakto difference in Kubernetes
Defakto issues short-lived attested cryptographic identities at runtime, so workloads authenticate securely without static tokens or manual PKI. Access is scoped to purpose, enforced by policy, and revoked when no longer needed. With Defakto, organizations can:
- Stop secrets sprawl
No database or API credentials stored in files or environment variables for attackers to exploit - Eliminate Vaults
Eliminate operational complexity. - Eliminate error-prone PKI processes
No tickets, CSRs, or manual certificate handling; lifecycle is fully automated - Unify identity everywhere
One consistent control plane spans clusters, clouds, and service meshes (like Istio) - Close the door on whole classes of attacks
By removing static credentials, Defakto eliminates the risk thread actors count on
Kubernetes enables speed and scale. With Defakto, security keeps pace.
Capabilities
Defakto’s Non-Human IAM Platform capabilities for Kubernetes
Business Outcomes
What you get when Kubernetes stops using secrets
When Kubernetes stops relying on secrets, risk goes down, compliance gets easier, and every workload aligns with your Zero Trust strategy.
Shrink cluster attack surface
No static secrets means nothing for attackers to steal. Reduced breach risk.
Eliminate the secret rotation treadmill
Never run a manual secret rotation campaign again.
Boost reliability and uptime
Automated certificate rotation prevents outages keeping clusters resilient at scale.
Bridge the gap between security and platform teams
Security gets control and visibility; developers run faster without credential friction.
Accelerate Zero Trust in Kubernetes
Identity-first security brings Kubernetes into alignment with enterprise Zero Trust strategies.
Eliminate credential debt
No more static secrets or overprivileged admin credentials reducing burden for engineering teams.
Simplify compliance and audit
Every action is auditable, making compliance and regulatory reporting available in real time.