Eliminate CI/CD Secret Sprawl. Secure Pipelines with Zero Static Credentials.
Replace static credentials in your CI/CD pipeline with just-in-time identity.
Challenges
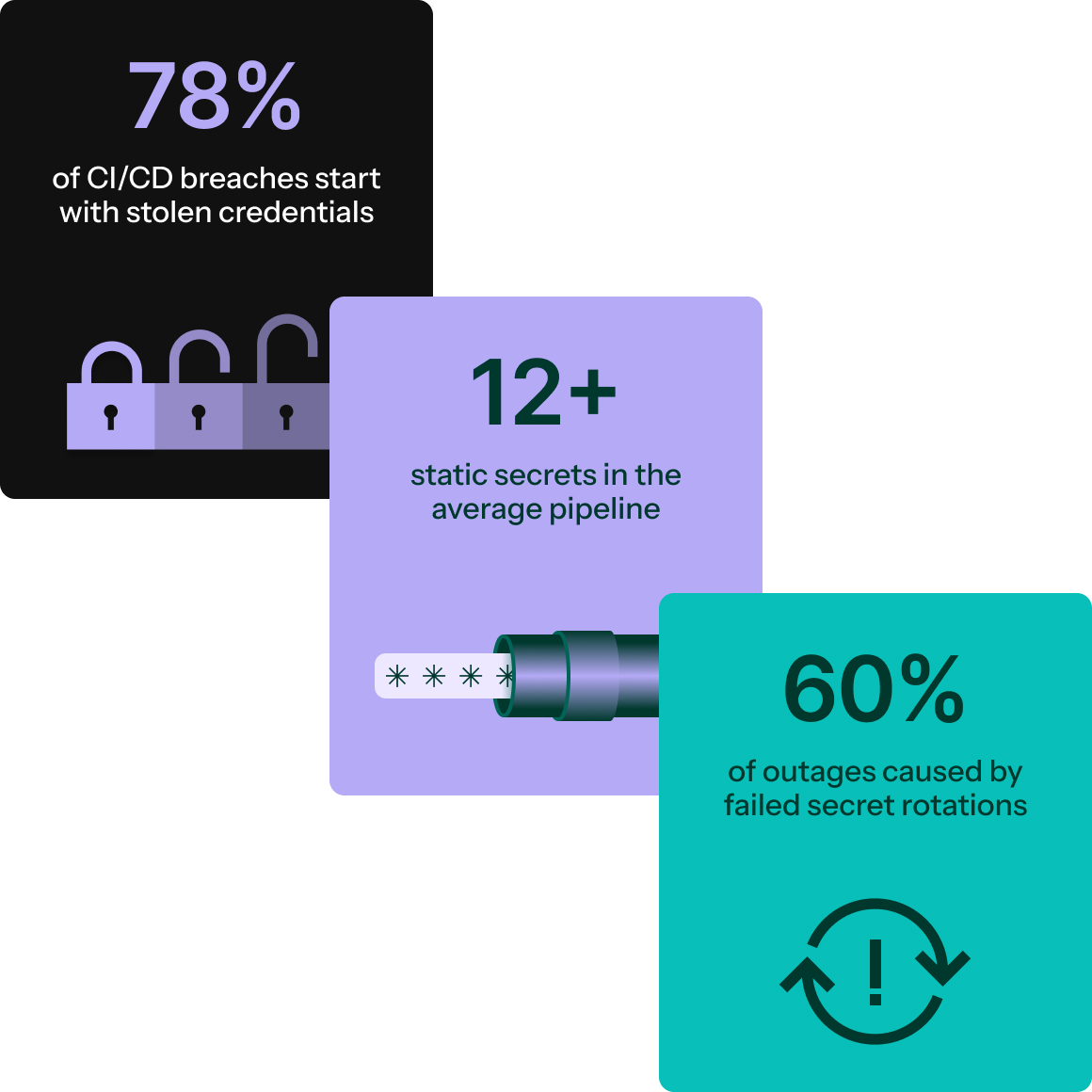
Static credentials are the weak link in CI/CD security
CI/CD pipelines are the engine of modern software delivery and they hold the crown jewels of your software supply chain for both dev and production. Yet most rely on static secrets like API keys and tokens stored in scripts, configs, or CI/CD secret stores. These credentials are long-lived, over-permissioned, and hard to track, turning your pipelines into prime targets for threat actors looking for a path to code, artifacts, and production.
Defakto eliminates hardcoded credentials, not velocity
Instead of embedding and managing secrets, Defakto issues short-lived, verifiable identities directly into pipelines. Credentials are created just-in-time, scoped to the job, and expire automatically when tasks end. Developers don’t need to create, rotate, or clean up credentials. Pipelines stay fast, secure, and auditable without the overhead of secret
The Defakto Difference in CI/CD
CI/CD pipelines are already a best practice. Doing the right thing shouldn’t make your life harder. With Defakto, it doesn’t.
Developers don’t need to manage credentials. Security teams don’t need to chase leaks. Defakto gives every CI/CD job its own identity that can be verified, scoped, and audited:
- No shared credentials across jobs
- No blind trust in runners or containers
- No default access assumptions
Access is created just-in-time, tied to the job’s purpose, and disappears when the job ends. It’s not a wrapper around secrets — it’s a completely different way to secure pipelines without slowing them down.
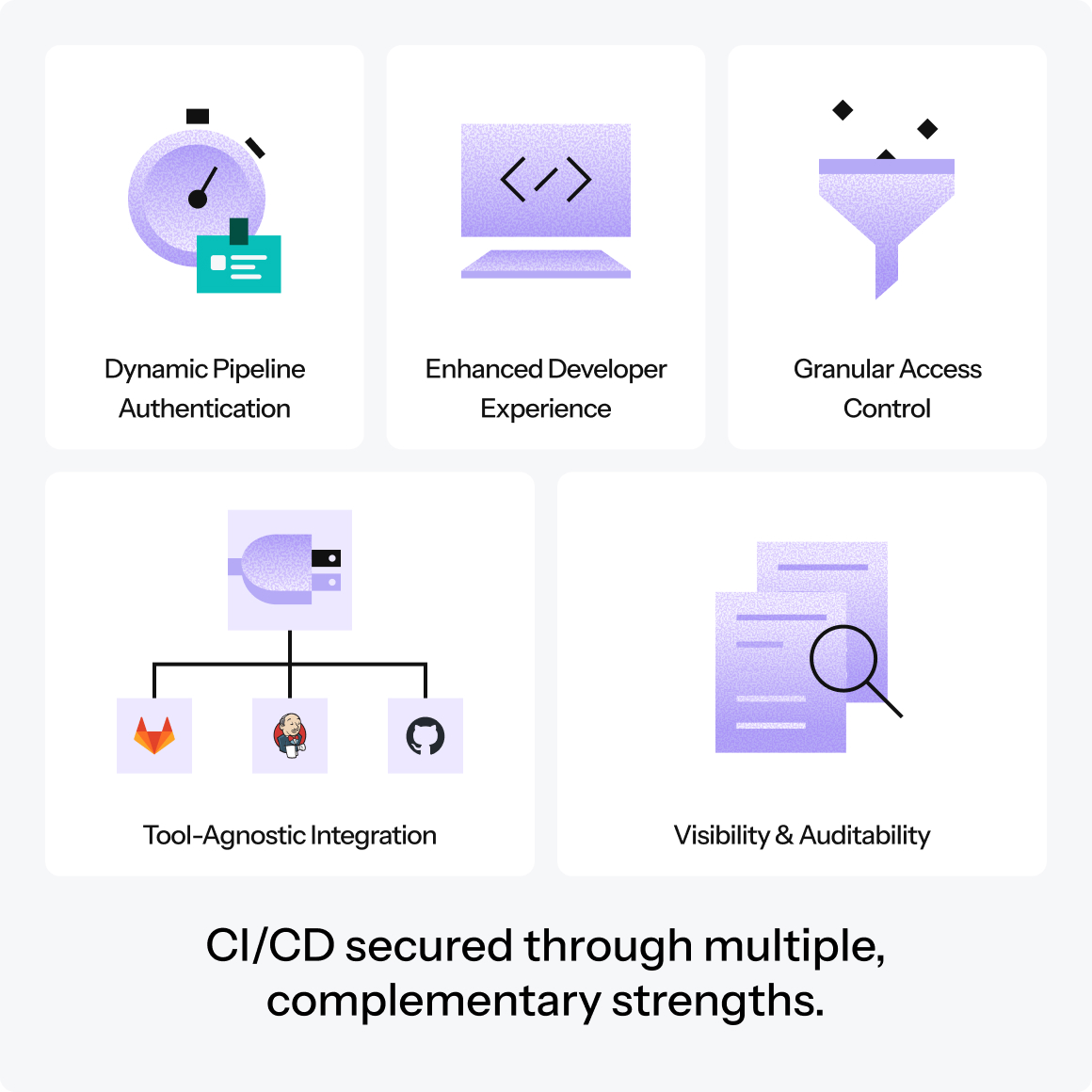
Defakto’s Non-Human IAM Platform capabilities
Defakto Business Impact
What you get when pipelines stop using secrets
Better uptime, less risk, and security that fits modern DevOps. Here’s what Defakto makes possible.
Maximize risk reduction
CI/CD pipelines hold the most sensitive secrets. Eliminating them delivers outsized ROI. Every job runs with short-lived, scoped access.
Prevent outages caused by credential failures
No more broken builds from expired tokens or misconfigured keys. Defakto grants access dynamically, when and where it’s needed.
Align security and development teams
Access is policy-driven and automated giving security control and visibility, while letting developers move fast without managing secrets.
Build Zero Trust from the inside out
Short-lived, policy-enforced identity ensures jobs only access what they should, when they should.
Eradicate credential debt at the root
Static credentials create risk to manage. Defakto eliminates them.