The Non-Human IAM Platform
From services and pipelines to jobs and AI agents, Defakto secures every non-human actor with verifiable identities issued in real time, preventing unauthorized access.
- No standing privilege
- No static credentials
- No identity debt
- No humans in the loop
Securing automated interactions from start to finish
Defakto continuously discovers unmanaged identities, replaces static secrets with dynamic credentials, and enforces policy in real time, enabling secure, autonomous infrastructure without development friction.
One console. Total control.
Defakto Console provides a single pane of glass for managing, monitoring, and securing every non-human identity. Teams can issue identities, govern, monitor, and enforce policy across all environments, including cloud, on-prem, hybrid, and AI.
Defakto Non-Human IAM Platform
Centralized visibility into every workload, API, service, and agent
Complete NHI
Lifecycle Management
Real-time governance and policy enforcement across environments
Ledger
Continuous discovery and governance
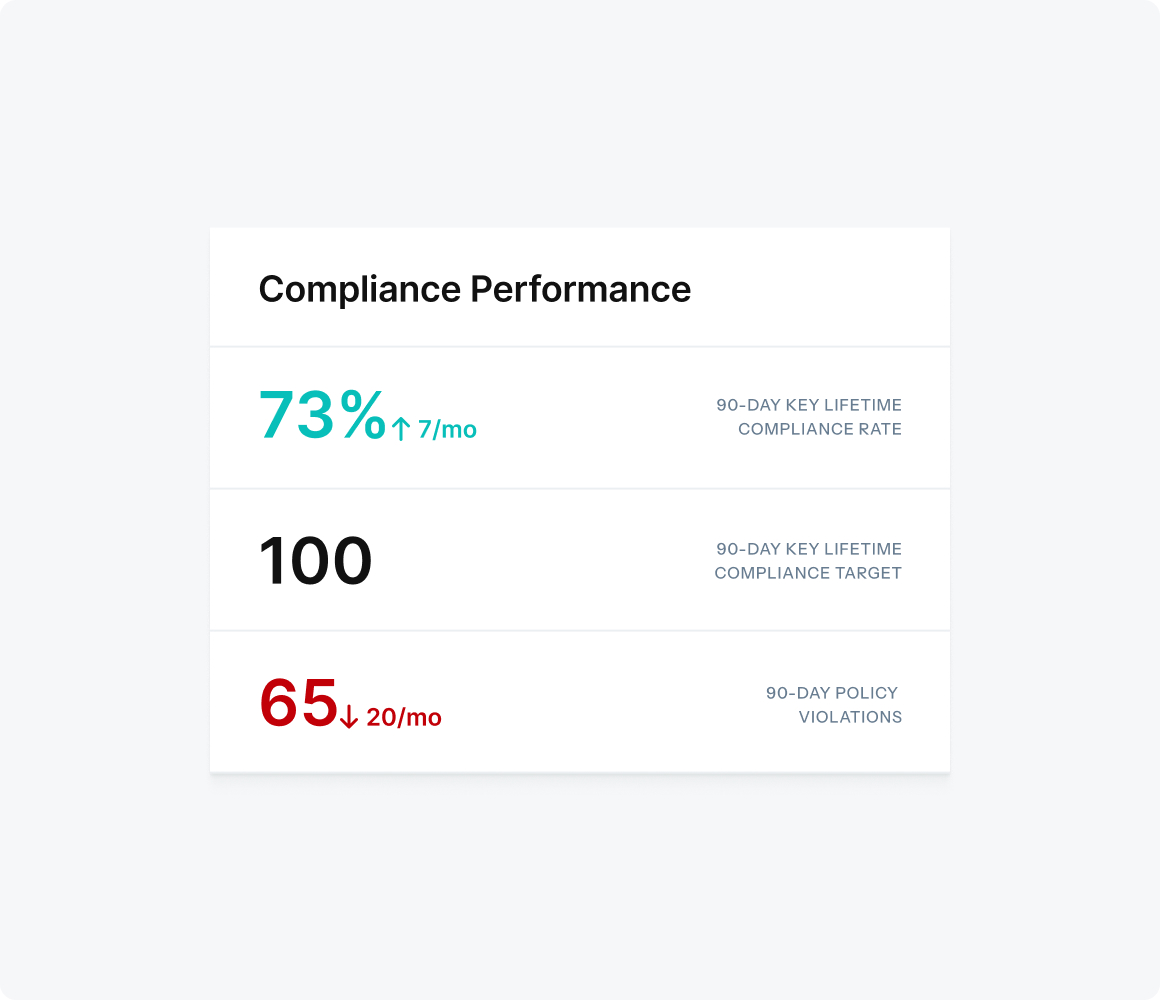
Ledger provides complete visibility and governance across the entire non-human identity lifecycle. Continuously discovers, catalogs, and assigns ownership so no identity goes unmanaged across your infrastructure.
- Real-time discovery of all non-human actors across clouds and on-prem
- Clear ownership and policy assignment for every identity
- Compliance-ready audit trails and reporting at scale
- Eliminate security blind spots by removing orphaned and unmanaged identities
Mint
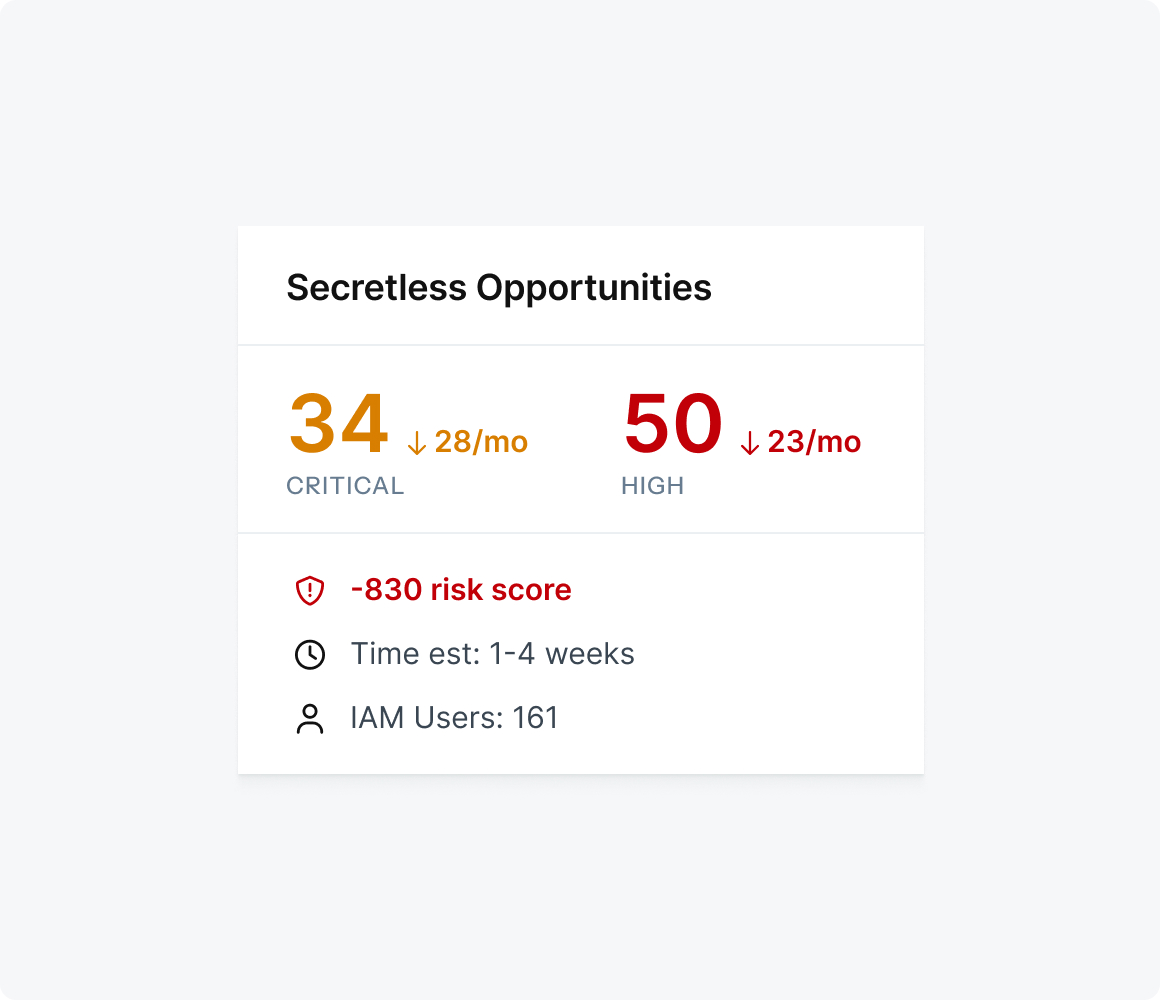
Issue secure identities to eradicate secrets
Mint replaces static secrets with cryptographically verifiable identities that are provisioned on demand. Every workload, API, and service gets the exact identity it needs and nothing more.
- Automated runtime issuance with no manual steps or tickets
- Short-lived, purpose-bound identities that expire when the task ends
- Remove vault complexity and secret rotation headaches entirely
How it works

Action initiated
Non-human actor starts an action

Context verified
Defakto verifies legitimacy with runtime context

Policy evaluated
Identity issuance policy checked in real-time

Identity issued
Defakto creates short-lived identity

Access authenticated
Action is authenticated and fully logged
Trim
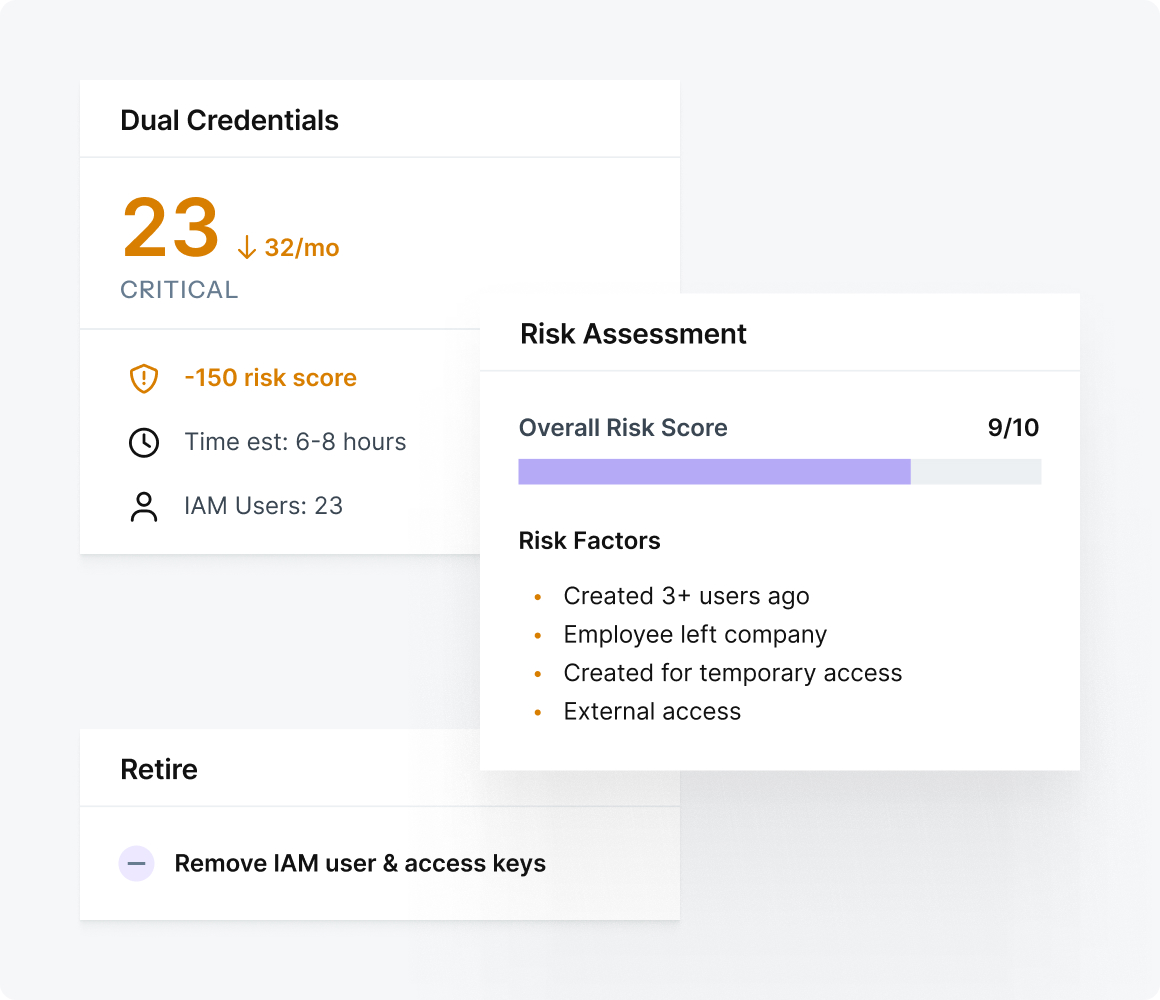
Right-size access to eliminate overprivileged service accounts.
Trim continuously enforces least privilege for all non-human identities. By detecting and eliminating overprivileged service accounts, it minimizes attack surface while keeping systems agile and secure.
- Identify and reduce overprivileged service accounts automatically
- Real-time policy enforcement that adapts as systems change
- Prevent lateral movement and insider risk before it starts
Mind
Identity security for AI agents
Mind extends Defakto’s non-human identity platform to AI agents and LLMs. Every AI system gets the same secure, dynamic identity model as your other workloads.
- Replace static LLM API keys with dynamic, verifiable identities
- Control what agents can access with precise, scoped policies
- Complete audit trails for every AI action and decision

Ship
Eradicate secrets from CI/CD pipelines
Ship replaces hardcoded credentials with dynamic identities for every build, job, and deployment. Secrets are never stored, rotated, or exposed — they simply don’t exist.
- No more vault complexity or config files vulnerabilities
- Zero friction for developers, maximum security for operations
- Accelerate delivery with dynamic, ephemeral identities
Build for security, engineering and IAM teams
Security Teams
- Remove secrets and standing access
- Stop lateral movement at runtime
- Attribute every action to identity
- Enforce Zero Trust by design
Engineering Teams
- Secure systems without slowing delivery
- Replace secrets, no code changes
- Reduce outages from misconfigurations
- Unblock devs from managing credentials

IAM Teams
- Replace service accounts with ID
- Automate identity lifecycle
- Prove access, policy, and logging
- Standardize control across systems


Built to integrate
everywhere
Defakto integrates with:
- Any Environment: AWS, GCP, Azure, on-prem
- Any Applications: Jenkins, Docker, GitHub, BuildKite, Istio, Kubernetes, AI agents
- Any Compute Infrastructure: VM, bare metal, Kubernetes, Serverless
Built for hybrid and multicloud.
Proven standards at the core. Confidence at scale.
Defakto is built on SPIFFE (Secure Production Identity Framework for Everyone), the industry-proven standard for secure workload identity. Our team helped create SPIFFE to ensure every workload gets a cryptographically verifiable identity at runtime.
With Defakto, customers gain:
Why enterprises choose Defakto
Other platforms manage identity debt. Defakto eliminates it.
Most modern tooling still clings to static secrets, overprivileged service accounts, and manual cleanup.
Defakto wipes the slate clean. No secrets. No service accounts. No standing access. Just real identity issued in real-time, scoped to the task, and impossible to misuse.

Enterprise ready
Built for scale, performance, and compliance.
Debt-free by design
No secrets. No service accounts. No long-term credentials to manage, rotate, or audit.
Built for brownfield + greenfield
Secure what you have and scale what’s next with zero friction.
Modern security without rewrites
Replace legacy access models without touching your apps or pipelines.
The result
Real security that works with your existing stack, scales with your growth, and adapts to whatever comes next. No vendor lock-in. No architectural rewrites. Just proven identity security that enterprises trust.